01: Intro to keeping shit secret
Introduction to information security. Old school crypto.
Keypair Hash PKI Certificate SSL\/TLS Plain text Message to encrypt Cipher Text Encrypted Message Key Secret that transforms plain text to cipher text Keyspace Possible set of keys regular symmetric key
Security rules
1: Don't roll your own software implementation\/crypto primitives
don't make your own software implementation or cyptographic primitives! you're not a highly experienced security designer\/implementer!!!
Kerckhoff's Principle
- even if algorithm is known, crypto system should be secure!
- system should depend on secrecy of the key, NOT the algorithm!
Historical Ciphers (stream ciphers)
Caeser Cipher
- encrypt by shifting letters down the alphabet, decrypt by shifting back
- FLAW: freq still same, b\/t encrypted and unencrypted
- FLAW FIX: remove spaces
- rings with letters on top of other rings with letter => 25 non trivial encryptions

Vigenere Cipher
- Write message, passphrase underneath (repeaet as necessary)
- add message to password mod 26 (start count @0)
- FLAW: if you know the passcode you know the message (frequency not a problem)

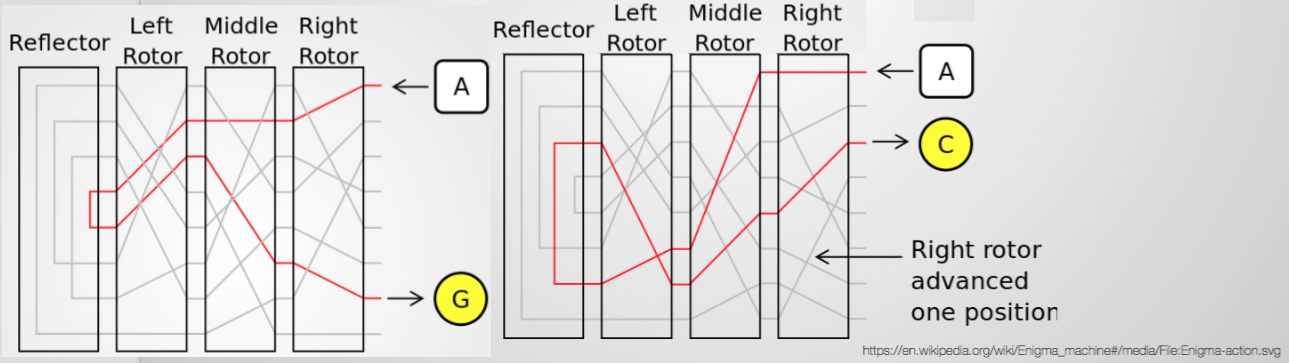
Enigma
- key press closes circuit, lighting up a cipher text, each key press rewires the machine
- keys changed on a regular basis
- FLAW: human error and subtle design flaws (A letter cannot go to itself - what plaintext ISN'T)
- 26^3 possible keys, with everything else, 2^70 - able to brute force
One-time Pad
perfect secrecy - no amount of computers can help since cipher text can decrypt to ANY message given corresponding pad, and all pads are equally as likely
- pad is chosen independently at random
- pad is exactly as long as the message
- pad only ever used once
not practical:
- generating and storing pad...
- |pad| = |message|
- human error (pad reuse, alignment, etc.)